-

View all news of Payoneer
Posted on September 30, 2019A Quick Guide to SEO on Amazon
What does SEO mean to you? It’s likely that Google comes to mind, given that the search engine receives roughly 63,000 searches per second, and holds 90.46% of the search engine market share worldwide.
If you’re an eSeller on Amazon and want to outrank the competition you need to ensure that your products are being found in searches and that they’re indexed. Every month more than 197 million people around the world get on their devices and visit Amazon, and in 2018 alone, Amazon’s share of the U.S. eCommerce market hit 49%.
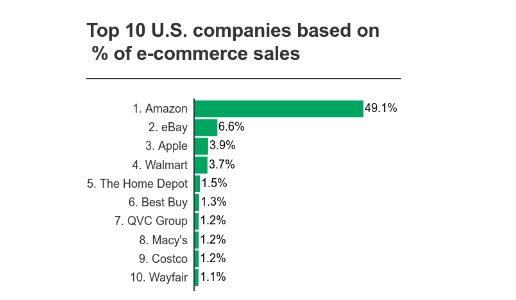
Source: emarketer.com
Want a piece of that profitable pie? Here’s how…
Amazon’s A9 Search Algorithm
Amazon’s search algorithm known as A9 works differently than any Google or Bing algorithm in surfacing results, so understanding exactly how it operates is important.
Simply put, A9 is composed of a variety of factors that are used to match users’ searches to products they’re most likely to purchase. As an eSeller, you know that the biggest challenge isn’t necessarily your competition as much as it is getting your products found through those searches.
Note that according to data from Amazon:
- 70% of Amazon customers don’t ever click past the first page of search results
- 35% of Amazon shoppers click on the first featured product they see
- The first three items displayed in search results account for 64% of clicks
- 81% of clicks are on brands on the first page of search results
A9’s main goal is converting a sale and if there’s one thing to know about Amazon’s SEO, it’s that it cares about buyers and selling to them. It sounds obvious, but it’s important to remember when optimizing your product listings. There are a variety of factors that influence A9. According to Amazon:
“Customers must be able to find your products before they can buy your products. Search is the primary way that customers use to locate products on Amazon.
Customers search by entering keywords, which are matched against the information (title, description etc.) you provide for a product.
Factors such as degree of text match, price, availability, selection, and sales history help determine where your product appears in a customer’s search results.”
Next thing you have to understand is keyword indexing.
What is Amazon Keyword Indexing?
Being indexed means that when users type a keyword into the search bar on Amazon, it will bring up your product on the search results. The more you’re indexed for highly relevant keywords, the more traffic and sales you will get.
Increasing the number of keywords, you’re indexed for increases the ways your customers find your products, but conversely, you miss out on potential traffic if you’re not indexed for as many highly relevant, purchase intent keywords as possible.

The key word is “relevant.”
You don’t want to cram dozens of keywords for every single product in hopes that something sticks. In fact, because Amazon rewards conversions and sales, traffic that does not result in conversions actually makes your products less appealing to A9, so relevant keywords are critical to your success.
Focus on keywords that will attract future buyers, check your keywords often for relevancy and conversions, and adjust accordingly. Fortunately, there are also steps you can take in addition to keywords to optimize your Amazon SEO.
How to Make the Most of Your Product Listings
Keyword research will always be at the heart of Amazon optimization, as their goal is to serve the most relevant products to searchers. The only way your product can be found for a specific search query is if the product listing contains the keyword searched, so make a master lists of relevant keywords.
Now that that’s done, you’re probably wondering, “How can I improve my ranking?”
Your Listing’s Title
Your product title is the part of your listing that will either make or break your ranking when it comes to product performance in search. It should contain:
- Brand
- Product line
- Material or key feature
- Product type
- Color
- Size
The order in which you place these elements is important, as the algorithm correlates higher relevance with keywords that appear earlier in the title. A good formula to follow includes:
[Brand Name] – [Product Type] – [Feature #1] – [Feature #2] – [Feature #3] – [Size, etc.]
Optimize Product Bullets and Descriptions
The next most important factor is highlighting your product’s features and describing your product in a way that presents the benefits — something Amazon takes very seriously.
Remember that master list of keywords? The ones that weren’t used in the title should be worked into the bullets. Some tips for optimizing bullet points include:
- Highlight the top five features that you want your customers to consider, like warranty information, dimensions, or age appropriateness
- Be as specific as possible with product features and attributes
- Don’t include price, shipping, or company information
This is your chance to tell a bit about your brand and product, while adding in some valuable keywords you want indexed. Remember that if they’re reading the description, they’re already on your product page. Now is the time to include a strong call to action.
Focus on the user experience by using a more conversational voice that focuses on how the product will enhance that customer’s life. Adding in a few lifestyle images of people using your product in some way can also help amplify conversions. Here you can tell a complete story and get your audience to connect with you and your product.
Optimize Amazon Backend Keywords
As the name implies, back-end keywords are keywords that aren’t found on the front- end, which gives you the chance to get more creative. While these keywords aren’t visible to customers, they still get indexed just like the terms in your bullets and description and are a great way to target long-tail keywords.
Some tips include:
- Including alternate spellings
- Adding in related search terms
- Thinking of creative, out-of-the-box queries that are related to your niche
While customers never see these keywords, they are instrumental in pushing your listings to the top.
In conclusion, one of the easiest solutions to make your product easy to find on Amazon is to make sure that it’s appropriately indexed. Not only does it help increase your organic ranking, but it also allows you to decrease your reliance on advertising or paid search when selling your products on Amazon.
By putting these suggested steps into action, you’re well on your way to increasing your ranking and increasing your sales!
The post A Quick Guide to SEO on Amazon appeared first on The Payoneer Blog.
-

View all news of BOKU
Posted on September 25, 2019Do SMS OTPs Solve Strong Customer Authentication (SCA)?
This week, the Financial Conduct Authority (FCA) confirmed the phased roll-out of PSD2 SCA within the UK. As part of this phased approach, it is envisaged that as of March 2020, merchants will be allowed to introduce 2-Factor Authentication as an approved method to achieve SCA compliance. However, to ensure full compliance, merchants must ensure their plans are completely in place by March 2021.
The introduction of SCA by the EBA (European Banking Authority) is expected to reduce the levels of financial fraud online, which significantly impacts the global e-commerce marketplace. However, due to concerns about the ability of Issuers, Acquirers, Gateways and Merchants to deploy 2-Factor Authentication by the original 14th September 2019 deadline, the FCA has agreed to allow the use of EMVCo 3DS 2.+ (Risk Based approach) alongside one form of authentication. SMS OTP is the primary form of authentication suggested by the FCA due to the potential availability to consumers.
Is SMS OTP the Mag Stripe of the e-Commerce World?
There are meaningful concerns within the e-commerce world around the security of SMS OTP, particularly with regard to social engineering and hacking vulnerabilities. The SMS delivery mechanism – sending a message directly to a consumer’s phone – introduces a new vector that fraudsters can attack to take over individual consumers’ accounts and commit fraud. Read full post
The post Do SMS OTPs Solve Strong Customer Authentication (SCA)? appeared first on Boku Inc..
-

View all news of BOKU
Posted on September 11, 2019Jack got Hacked: Why SMS OTP is a Dangerous Consumer Verification Method
You may have missed the story as you were leaving early last Friday for the long holiday weekend: Jack got hacked.
Jack, of course, is Jack Dorsey, CEO and co-founder of Twitter and Square. And ‘hacked’, in this instance, means that there were a number of inappropriate tweets that seemingly originated from his personal Twitter account. Twitter “regained control” of the account after about 15 minutes, but the damage was already done.
It’s worth examining exactly how the hackers gained access to Jack’s personal Twitter account. One might suspect that the highly visible CEO of a technology company would have best available security safeguards in place, and that any “hack” aimed at such an individual would require a tremendous amount of technical skill, coordination and resources.
Those suspicions would be wrong. The technique the hackers used was surprisingly simple and shockingly prevalent, especially in markets that have a majority of users with pre-paid mobile phone services: a SIM swap.
A SIM swap occurs when a fraudster, using a victim’s personal information gleaned off the dark web or other available sources, calls the victim’s mobile network operator (AT&T or T-Mobile, for example), and impersonating the victim, has the mobile network operator transfer the victim’s phone number to a different mobile device that is in the fraudster’s possession. Read full post
The post Jack got Hacked: Why SMS OTP is a Dangerous Consumer Verification Method appeared first on Boku Inc..
-

View all news of BOKU
Posted on September 11, 2019Why Layering Is Going Out Of Fashion In Consumer Authentication
For those worried about the security of identity in the age of mobile, the last few weeks have not exactly been an encouraging time to be reading the headlines. Google’s Project Zero, an in-house team tasked with finding and publishing security and privacy vulnerabilities it finds in public software, released a blog post detailing major security holes it had discovered in iPhone software going back two years.
The flaws have been fixed since February, but industry watchers were bewildered that such exploits had sat out there for so long and that Apple had needed an outside team to discover it.
Also, bewildering was the fact that Google finding a hole in Apple’s security was the second most attention-grabbing security failure last week. The unfortunate distinction of first place went to Twitter CEO Jack Dorsey, who was a victim of a SIM Swap attack that left his Twitter account spewing racist invective for about 20 minutes.
It was a hard week to feel particularly secure on a mobile device, Karen Webster observed in a recent conversation with Boku CEO Jon Prideaux, as it was easy to get the feeling that an identity thief is hiding around every corner — and perhaps in every text message or Tweet to boot. Read full post
The post Why Layering Is Going Out Of Fashion In Consumer Authentication appeared first on Boku Inc..
-

View all news of Gocardless
Posted on August 14, 2019What does Strong Customer Authentication (SCA) mean for your business?

What is SCA regulation?
For the most up-to-date analysis and guide to SCA, view The complete guide to SCA for businesses
On 14 September 2019, Strong Customer Authentication (SCA), a new regulation for authenticating online payments, will be rolled out across Europe, as part of the Second Payment Services Directive (PDS2).
(Note: On 13 August 2019 the Financial Conduct Authority (FCA) confirmed that enforcement of SCA in the UK will include a phased 18-month implementation, starting on 14 September 2019 and ending March 2021.)
One of the key aims of SCA is to reduce the incidence of payer fraud and increase security, by introducing two-factor authentication on electronic payments.
Learn more about how SCA works.
What kind of transactions are affected by SCA?
SCA comes into force on 14 September 2019, and will affect any applicable transaction for businesses whose payment service provider is located within the European Economic Area (EEA) and whose customer's bank or card provider is also located within the EEA. If only one of those parties is located within the EEA, the requirement is for them to still use 'best efforts' to apply SCA.
(Note: The FCA released a statement on 28 June 2019 recognising concerns around the industry's preparedness and ability to comply with the requirements for SCA by 14 September 2019.)
SCA does not apply to GoCardless’ Direct Debit payments service. GoCardless is fully PSD2 compliant, and SCA does not apply to payments made through GoCardless as it uses 'paperless' Direct Debit mandates, which are out of scope of SCA.
So, what transactions are affected by SCA?
The main type of transactions that will be impacted are card payments made over the internet. As of next year, all single electronic payment transactions will need to be authenticated by at least two of the three following methods:
- Knowledge: something only the user knows, such as a password.
- Possession: something only the user possesses, such as a token or mobile phone.
- Inherence: something the user is, such as a biometric element (e.g. fingerprint recognition).
According to Mastercard research, just 1-2% of UK online transactions require cardholder authentication to ensure completion (most likely using a password), but this is set to rise to up to 25% from this autumn.
SCA will also apply to some contactless transactions, as a periodic check to ensure the card is being used by its rightful owner. In-store chip and PIN transactions are already compliant.
Exemptions to SCA
Several exemptions and out of scope transactions exist under SCA. These have the potential to benefit businesses with recurring revenue. Notable exemptions or out of scope transactions include:
- Merchant-initiated transactions
- Fixed recurring transactions and subscriptions
- Transactions below €30
- Trusted beneficiaries (whitelisting)
- Corporate payments
- Low risk transactions
For more information, see our detailed list of all key SCA exemptions.
Where do subscription businesses stand?
For subscription businesses taking recurring payments by card, SCA will apply at least to the initial setup of the Continuous Payment Authority for the recurring card transaction. For recurring payments of the same amount, SCA will not need to be applied again. If this amount changes, SCA will typically need to be applied again, unless the payment is initiated by the merchant and the amount being charged is within reasonable expectations of the customer.
In most cases it will be the payer’s bank that facilitates the authentication, with the payer’s payment service provider facilitating the additional steps in the payment journey. Though where this is not the case, payment service providers affected by the regulation (e.g. card providers) will be expected to provide the authentication mechanisms themselves.
The impact on business
Any initiative to tackle the serious problem of fraud should be welcomed, especially since the e-commerce revolution shows no signs of slowing down.
Almost five million people in the UK had money stolen from their bank or credit card account last year, according to Compare the Market. Around £2 billion was taken from about one in ten people in the UK, with online payments being the weakest link – over a quarter of frauds took place online last year.
But the impact of SCA is likely to be felt more widely than in fraud incidence numbers. It could also impact costs and conversion for businesses, says Duncan Barrigan, GoCardless’ VP, Product.
“We’re yet to see the full impact of SCA, but the implications are potentially significant. Businesses are likely to see fewer customer chargebacks, and therefore potentially a reduction in operating costs.”
“Though they could see cost increases elsewhere,” he adds. “For example, if we see a liability shift, where the payer’s service provider is liable for fraud and chargeback costs, we could feasibly see increased fees as a result.”
Balancing risk and conversion
While the implications on operating costs are not yet clear, many businesses are concerned that SCA could be a conversion killer.
Additional payment authentication can introduce friction to customers’ online journeys by requiring additional steps in the payment process.
“For businesses taking payments online, there is a continual balancing act between risk and conversion,” says Duncan. “At the extremes, you could have the most friction-free offering out there; this would be completely open but also vulnerable to fraudsters. Or you could create the most secure service in the world. Ultimately, however, the barrier to entry would be so high that no one would want to use it. It’s important to find the right balance for each business.”
Learn more about how your customers will react to additional security measures.
What SCA means for GoCardless
As we mention above, SCA doesn’t apply to GoCardless’ Direct Debit payments service, and GoCardless is fully PSD2 compliant. We continue to take security and fraud prevention seriously, and GoCardless’ Risk and Product teams are committed to getting the balance between conversion and security right for our customers.
“We believe that technology and data can make it possible to improve the trade-offs merchants face between risk and conversion,” says Duncan. “At GoCardless, we’re working on a payment experience that will enable our customers to benefit from these advances whilst being able to adjust their risk appetite, to suit their business needs.
“Finding a way to reduce risk intelligently with the smallest possible negative impact on conversion rates is the best pay off for everyone involved.”
Fore more information on SCA, see our FAQs.
-

View all news of BOKU
Posted on August 8, 2019Why Mobile Phones Are The Better Consumer Authentication Mousetrap
At this point in 2019, we’ve all dealt with some flavor of two-factor authentication that uses SMS one-time passcodes. We attempt a sign-in and see a prompt that tells us that a six- (or nine, or four) digit PIN is being texted to us, and that we have to enter it to proceed with our login or password change. It’s a mild piece of friction, but it’s not terribly onerous and is doing something useful: keeping consumers safe.
Unless, of course, it isn’t. SMS one-time passcodes are more of a risk than most consumers realize, Boku CEO Jon Prideaux told Karen Webster in a recent conversation. The consumer thinks their bank is sending them a unique code that only they can directly access — but the reality is a little different.
A fraudster doesn’t always have to hack a phone to access a user’s identity and information — they can hack the person. Read full post
The post Why Mobile Phones Are The Better Consumer Authentication Mousetrap appeared first on Boku Inc..
-

View all news of Gocardless
Posted on July 29, 2019RGDP, le bilan un an après : 5 choses que nous avons apprises sur la mise en place d'un programme de confidentialité

Vous vous souvenez quand le RGPD est entré en vigueur l'année dernière et que toutes les entreprises avec lesquelles vous aviez un jour été en contact ont décidé de vous envoyer un e-mail ?
Certaines ont demandé votre consentement, d'autres se sont contentées de vous envoyer un simple message. Le mieux informées, ou celles qui avaient bien pris en compte tous les conseils donnés, n'ont rien envoyé du tout, convaincues que leurs solides pratiques en matière de respect de la vie privée appliquées dans la période précédant le RGPD justifiaient ce non-envoi.
À l'époque, nous avions partagé les détails de notre programme de confidentialité. Un an plus tard, nous avons pu le mettre à l'épreuve. Nous avons découvert ce qui fonctionne et ce qui ne fonctionne pas. Les directives réglementaires, les événements ainsi que la mise en application nous ont permis de mieux comprendre ce qui est efficace pour le RGPD.
Pourtant, depuis l'an dernier, tous les événelents et tables rondes auxquels j'ai participé tournent inévitablement autour d'un seul et même sujet...
Comment gérer la confidentialité à grande échelle ?
Comment se conformer à chacun des éléments prescriptifs du RGPD tout en respectant les principes de la réglementation, et ce, sans rajouter de distractions inutiles à votre activité principale ?
En résumé : comment s'assurer de prendre en compte la vie privée dès la conception (« privacy by design ») ? Les experts en confidentialité ne sont pas des plus nombreux et peu d'entreprises peuvent se permettre d'en embaucher assez pour répondre à toutes les exigences du RGPD. De plus, si les programmes de confidentialité sont conçus séparément des processus opérationnels normaux, il est impossible de le faire évoluer avec l'entreprise.
Dans cet esprit, voici cinq choses que nous avons apprises au cours de l'année passée concernant l'intégration de la confidentialité en entreprise.
1. Parlez la langue de votre entreprise
Tout le contraire de ce que nous avons fait à l'arrivée du RGPD. Pour nous assurer que notre registre des traitements était conforme au RGPD, nous avons préparé et envoyé des questionnaires d'un outil prêt à l'emploi avec toutes les questions auxquelles nous avions pensé à toutes nos équipes de traitement de données. Toutes sauf les bonnes.
« Pouvez-vous identifier une base légale de traitement pour cette activité ? », « Comment respectez-vous le principe de limitation du but pour cette activité ? »
C'est en nous penchant sur notre registre de conformité au RGPD que nous nous sommes rendu compte que nous avions tout faux. « Je ne suis pas sûr » était la réponse la plus fréquente à la plupart des questions !
Pour la version 2.0, nous avons adopté une approche différente et avons décidé de poser uniquement des questions auxquelles nous savions que nos équipes pouvaient répondre, telles que : À quelle fin utilisez-vous ces données ? De quelles données avez-vous besoin pour le faire ? Quels systèmes vous aident à réaliser cette tâche ? Grâce à ça, nous avons établi un registre clair, exploitable et facile à maintenir à jour.
2. Soyez là où les choses se passent
Convoquer un expert en confidentialité à chaque réunion est impossible. Nous ne sommes pas assez nombreux et même si nous pouvions être partout tout le temps, cela ralentirait toute la procédure.
Par conséquent, quasiment tous nos employés devront, à un moment donné, prendre des décisions en rapport avec la confidentialité... comme évaluer un nouveau produit, choisir un nouveau fournisseur ou expérimenter un nouveau modèle de données.
J'ai vu des programmes de confidentialité très bie, conçus échouer simplement parce qu'ils n'ont pas été adoptés par les entreprises.
Lorsqu'on demande aux gens de faire quelque chose en dehor de leurs tâches quotidiennes, ils ont tendance à prendre la « voie de la moindre résistance ». Cela ne veut pas dire qu'ils ne veulent pas faire les choses bien. Cela signifie que même s'ils comprennent ce que nous leur demandons de faire (cf. le point 1), la procédure peut être plus complexe qu'il n'y paraît pour eux.
C'est pourquoi pour pouvoir fonctionner, nous devons nous assurer que les procédures de confidentialité sont solidaires de nos activités habituelles. Comme l'explique notre responsable des données : nous devons faire en sorte que les gens puissent faire ce qu'on leur demande aisément et nous assurer que ce sera très dur pour eux de mal faire. Ce qui nous amène à notre troisième point...
3. Automatisez autant que possible
Cette évolution du domaine de la confidentialité a vu l'émergence d'outil prêt à l'emploi permettant d'automatiser la conformité.
Cependant, beaucoup de ces outils fonctionnent de façon indépendante. Par exemple : un outil de gestion des contrats de traitement de données qui ne peut pas être rattaché à nos fonctions de passation des contrats fournisseurs ; un outil de suivi des requêtes d'accès inutilisable par nos services d'Assistance ou encore un outil d'analyse d'impact sur la protection des données en dehors du cycle de vie du développement du produit.
Problème : lorsque ce type d'outils ne s'intègre pas dans vos activités, vos employés sont forcés de travailler à l'aveugle, ce qui signifie parfois faire mal les choses.
Pour bien faire, nous pensons qu'il faut commencer par vous pencher sur votre entreprise et ses besoins : À quoi ressemble votre quotidien ? Quels documents créez-vous, quels outils utilisez-vous, quelles sont vos étapes de prise de décision ?
Avec ces informations, vous pourrez vous poser les bonnes questions au bon moment et serez en mesure de faire remonter vos questions et besoins à l'équipe de protection de la vie privée si nécessaire.
Par exemple, lorsque nos équipes de données créent une nouvelle fonctionnalité, notre procédure leure demande automatiquement d'identifier un objectif commercial, il est impossible de lancer la création de cette fonctionnalité. Si l'objectif n'est pas répertorié dans le registre, cela signifie qu'il faut réexaminer la confidentialité afin d'intégrer ce nouveau type d'objectif.
Cette procédure nous fournit également une piste d'audit que nous pouvons tester pour nous assurer que les bonnes décisions sont prises.
4. Méfiez-vous des remèdes miracle
L'automatisation des procédures de confidentialité peut finir par vous nuire. Certaines entreprises utilisent des listes de contrôle pour garantir l'évolutivité de leurs programmes de confidentialité. Mais cette approche peut se retourner contre vous.
Mal appliquées, les couches de bureaucratie privent les employés de leur pouvoir, les empêchent d'être responsables de leur impact sur la vie privée et génèrent des risques inattendus (« cela ne figurait pas sur la liste de contrôle donc ça ne peut pas être un problème »).
Nous avons veillé à ce que nos procédures soient simples et avons mis l’accent sur la formation et l’orientation de nos équipes.
Par exemple, nous avons créé une formation pour nos responsables Produit et Fonction. Cette formation leur fournit les ressources nécessaires pour travailler à l’intégration de la confidentialité dans nos produits de bout en bout.
Parmi toutes ces ressources, l’une d’entre elles a été particulièrement utile dans la définition de produits et l’évaluation de l’impact sur la confidentialité : une taxonomie sur-mesure des risques de confidentialité qui permet d’orienter les discussions sur la réduction des conséquences non intentionnelles ou illégales de l’utilisation de données à caractère personnel.
5. Écoutez ce que vos programmes vous disent
Le RGPD permet aux personnes concernées d'exercer leurs droits auprès du contrôleur des données. Les requêtes d'accès et de suppression sont les deux requêtes que nous recevons le plus souvent.
Afin de ne pas surcharger notre équipe de confidentialité, nous avons décidé qu’elles seraient d’abord traitées par nos agents du service clientèle dans leurs propres outils (macros Zendesk et Centre d’assistance) avant d’être envoyées dans notre logiciel de demande de droits pour en assurer le suivi.
Nous sommes fiers de dire que cela a très bien fonctionné. Premièrement, nous ne traitons pas ces demandes de façon isolée. Envoyer d’abord ces requêtes à l’Assistance permet leur traitement par les personnes les mieux formées pour identifier et résoudre les problèmes sous-jacents (grâce aux formations et ressources fournies par l'équipe de protection de la vie privée).
Deuxièmement, notre équipe d’Assistance possède une grande expérience des métriques et des indicateurs de performance clés. L'utilisation de leurs outils nous permet de suivre de près les requêtes d’accès, ainsi que d'autres plaintes, questions et incidents.
La rapidité et l’efficacité avec lesquelles nous pouvons traiter une requête d’accès ou de suppression nous en dit long sur la santé de notre programme de confidentialité. D’ailleurs, le suivi de ces métriques est l’un de nos principaux indicateurs de risque.
Nous suivons également les taux de désabonnement marketing, les analyses de risque des fournisseurs ainsi que le temps nécessaire pour répondre aux demandes juridiques liées aux données.
Ainsi, nous comblons nos lacunes, nous améliorons progressivement notre programme et nous nous conformons au principe de responsabilité, le concept phare du RGPD.
Et vous, quels conseils avez-vous pour mettre en place un programme de confidentialité ? Rejoignez-moi sur LinkedIn pour continuer cette conversation.
-

View all news of BOKU
Posted on July 23, 2019Navigating Identity’s ‘Big Canvas’ with Boku
The fundamental unit of trust in any transaction lies in identity — namely, ensuring that the person who shows up to transact is who they say they are. It’s also the most highly regulated part of any financial transaction.
“The identify verification that happens before accounts are opened are where governments and regulatory bodies very much tell you to do things in a certain way,” Boku CEO Jon Prideaux told Karen Webster in a recent conversation.
It’s a process that doesn’t leave much room for interpretation — either you are compliant or you’re not — and one in which companies tend to bring in a partner who can make the process of achieving and maintaining compliance less painful.
Yet it’s also a process that’s built around checking an individual’s credentials against various static data sources to confirm that person is who they claim to be and are not on any kind of watch list.
And it’s a process that, in a dynamic digital world, does not lend itself well to static data sources.
Prideaux told Webster that identity is a “big canvas,” and establishing the identity of parties is much more than a “one-and-done” check against a list. Making sure the person is authorized to use those credentials is critical to establishing trust — and it’s the sweet spot in which Boku operates. Read full post
The post Navigating Identity’s ‘Big Canvas’ with Boku appeared first on Boku Inc..
-

View all news of Paybyweb
Posted on July 18, 2019Website Updated
Check out our new site! We now offer lots WEBSITE UPDATED
WEBSITE UPDATED
of new features and services that were not
offered in the past
Web Design Services
Have an idea for a product or service? Paybyweb can help you get it on the Web. From obtaining your domain name to getting your site designed and published, we offer it all. We can have your site up in as little as a day or two. Simply provide us the images or content you would like. Your site can include a Home, Services, About Us, Contact, FAQ, Shopping Cart, Testimonials, and more.
Social Media Services
Gain traction on social media by letting Paybyweb help. We can get you noticed on a variety of platforms, including images, hashtags, and more. We can provide complete turnkey social media services to free you up to do more important tasks.
Accepting Credit Cards with a Merchant Account
Paybyweb has been a leading provider of merchant accounts to help companies accept credit cards for over 25 years. We can get you approved in as little as one business day.
Taking Electronic Checks
Since 1992, we have provided thousands of companies with the ability to accept checks electronically. Customers need not sign or mail their check. We even offer to deliver the checks to your bank and deposit into your acct..
Check out all we have to offer at www.PayByWeb.com -

View all news of Gocardless
Posted on July 17, 2019What does SCA mean for recurring payments?

If you’re a merchant based in the European Economic Area (EEA), you might already be aware of Strong Customer Authentication (SCA). If you’re not, we’ve written a brief overview of what the new European PSD2 law means for subscription businesses. In a nutshell:
- SCA is part of European PSD2 regulations, which aim to increase the security of electronic payments and account management, as well as reduce payment fraud
- SCA comes into effect on 14 September 2019
- If your business uses a European payment provider to serve customers within the EEA, SCA requires additional proof of identity from your customers when they make certain types of payments
Many businesses are concerned that the extra security measures posed by SCA will increase friction at checkout, leading to a drop-off in conversion. For businesses that take recurring payments, there are broadly three major factors that determine how SCA will affect you. And there are a number of exemptions and out of scope transactions that could help minimise impact on conversion rates.
Ahmed Badr, General Counsel at GoCardless, explores these areas in the videos below, as well as recommending the next steps businesses should take.
How does geography factor into SCA?
While your business and your payment service provider must allow for SCA to be applied, it is your customer’s bank (or card issuer) that will apply the authentication. Looking specifically at payments, and not other areas that SCA is required such as when accessing a payment account, the legislation is not limited in its geographical reach.
In recent guidance, the body responsible for SCA specifications has confirmed that SCA is only strictly required when both a merchant’s payment provider and customer’s bank (or card issuer) are located within the EEA. When only one of those parties is located within the EEA, it must use “best efforts” to apply SCA for payments that require it.
In practice, this means is that if a merchant located outside the EEA is using an EEA-based acquirer, that merchant can still expect the acquirer to support SCA for transactions that take place with EEA-based issuers.
How does payment method factor into SCA?
How you choose to accept payment from your customers impacts how SCA will affect you. SCA primarily targets electronic payments that are initiated by your customer, and that are processed instantly. This means many credit card and debit card payments, as well as bank transfers, will be subject to SCA.
Direct Debits or bank debits, on the other hand, are out of scope of SCA. This includes payments set up and made through GoCardless. The key difference with these payments is that the customer’s payment details are collected without the involvement of the customer’s bank, and this is being done at a different point in time to the payment being processed.
These payments also typically have much lower rates of fraud than card payments or bank transfers.
How does the type of billing factor into SCA?
Broadly speaking, recurring purchases can be billed in one of three ways:
- Invoicing - Your customer pays you variable amounts, at regular or variable intervals, with no fixed end date. (E.g. Professional services.)
- Subscriptions - Your customer pays you fixed amounts, at fixed intervals, with no fixed end date. (E.g. Gym membership.)
- Instalments - Your total product or service cost is broken down into fixed amounts, for your customer to pay at fixed intervals, with a fixed end date. (E.g. Loan repayments.)
Generally speaking, SCA applies to recurring purchases when either the amount or frequency of payments is changing. With invoicing, the amount varies, and thus every payment a customer initiates is subject to SCA. With subscription and instalment payments, only the first payment will be subject to SCA, as the subsequent payments are fixed amounts at a fixed frequency.
Which payments are out of scope of, or exempt from, SCA?
For businesses taking recurring payments, there are a few key exemptions and out of scope areas to be aware of.
Merchant-initiated transactions (MITs)
These are payments from your customer where you as the business initiate the transaction. In these cases, your customer must have given you advance authority to take recurring payments from them for a specified product or service.
Both card payments and Bank Debits like Direct Debit can be MITs. For card payments, SCA will typically also need to be applied when your customer provides you their payment details. However, all following transactions will be out of scope of SCA.
For electronic ‘paperless’ Direct Debits, such as those handled by GoCardless, SCA is not required even during mandate setup - due to the fact that the customer’s bank is not involved at the point of mandate setup. These types of payment also typically present a lower risk of payment fraud.
Learn more about merchant-initiated transactions.
Trusted beneficiaries (“whitelisting”)
As part of SCA, banks and card issuers will allow their customers to create a whitelist of businesses they trust, and for whom they are happy not have SCA applied. If your customer decides to add your business to their list of trusted beneficiaries, SCA will only need to be applied once - at the point of adding you to the whitelist. All of their future payments to you can then be processed without SCA.
Low value transactions
When your customer makes a payment to you that is under €30 (or its equivalent), it may be exempt from SCA.
There are two notable caveats to this. First, every sixth low value transaction your customer makes, SCA will need to be applied. This isn’t just every sixth payment they make to you, it covers all payments they make anywhere.
The second caveat is that if a cumulative payment total of €100 (or its equivalent) is reached before that sixth payment, SCA will need to be applied at that point.
Low risk transactions
If your payment service provider’s overall fraud rates are below certain thresholds, your customer’s bank can choose to not apply SCA under certain transaction values. For values above €500, however, this exemption does not apply.
Take note...
It’s worth noting that while banks are allowed to support exemptions under SCA, they aren’t obliged to. And even if a customer’s bank does support exemptions and a purchase meets the requirements of an exemption, they are still able to apply SCA if they wish. As such, you cannot rely on exemptions to opt out of preparing your payment flows for SCA ahead of September.
Learn more in our detailed list of all key SCA exemptions.
What next?
Take some time to map out your payment flows. Make sure you’re aware of every use case in your business and understand how SCA will apply to each of them.
While it is ultimately your customers’ bank or card issuer that will control SCA, the checkout flow on your website will need to capture the additional proof of identity from your customers. And, your payment service provider will need to be able to facilitate the secure transfer of this data to your customer’s bank or card issuer.
When you’ve mapped out all of your payment flows and understood the use cases where SCA applies, note any necessary changes you’ll need to make ahead of September to be compliant with the regulation. Also make sure you double check with your payment service provider to ensure they will be facilitating your compliance.
Over the coming months, we’ll be publishing more updates about SCA for businesses taking recurring payments. To ensure you don’t miss out, follow us on LinkedIn, Facebook, or Twitter, and keep an eye on our blog, guides, and support centre.
For now, make sure you read our comprehensive guide to Strong Customer Authentication.
(Note: On 13 August 2019 the Financial Conduct Authority (FCA) confirmed that enforcement of SCA in the UK will include a phased 18-month implementation, starting on 14 September 2019 and ending March 2021.)